![PDF] Private Data Acquisition Method Based on System-Level Data Migration and Volatile Memory Forensics for Android Applications | Semantic Scholar PDF] Private Data Acquisition Method Based on System-Level Data Migration and Volatile Memory Forensics for Android Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fc62f03cb6ad75b615252e8ea762d7402b2ea811/3-Figure1-1.png)
PDF] Private Data Acquisition Method Based on System-Level Data Migration and Volatile Memory Forensics for Android Applications | Semantic Scholar

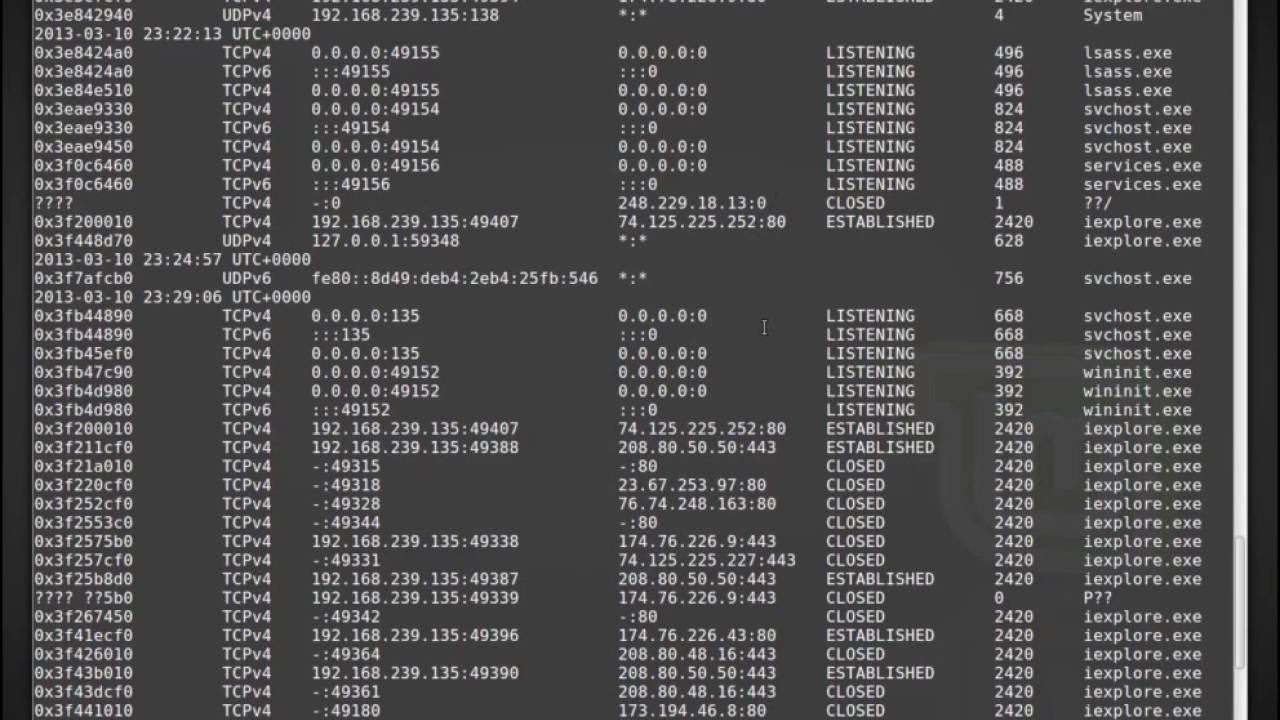
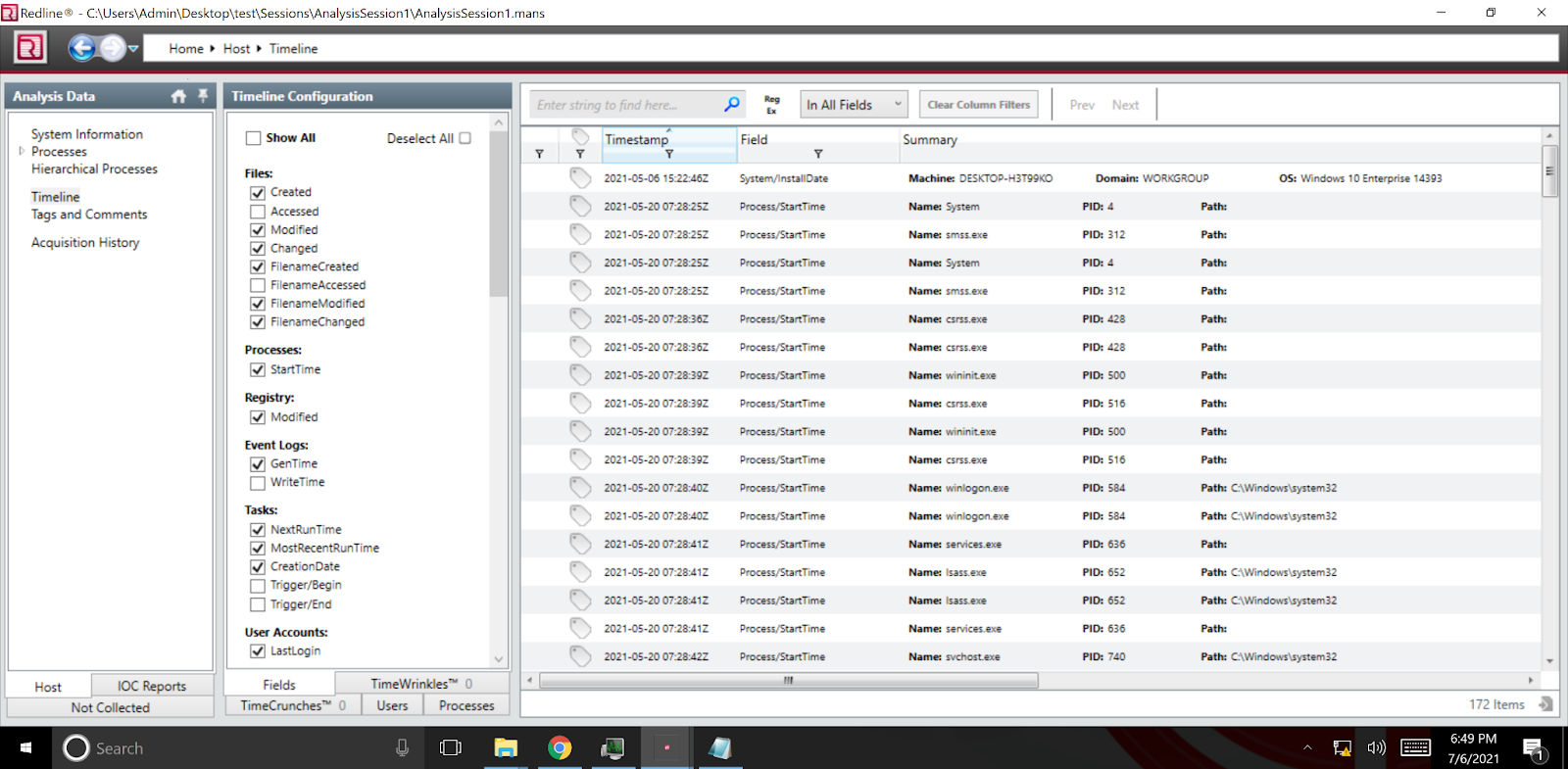
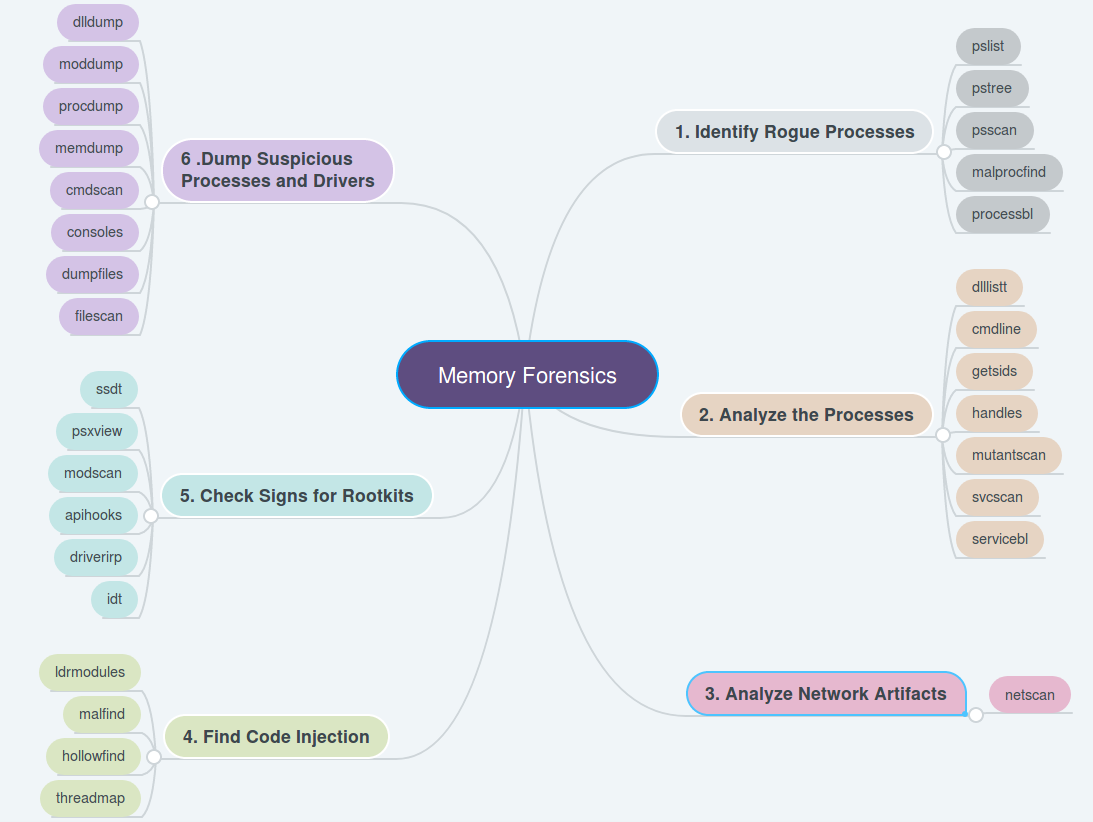
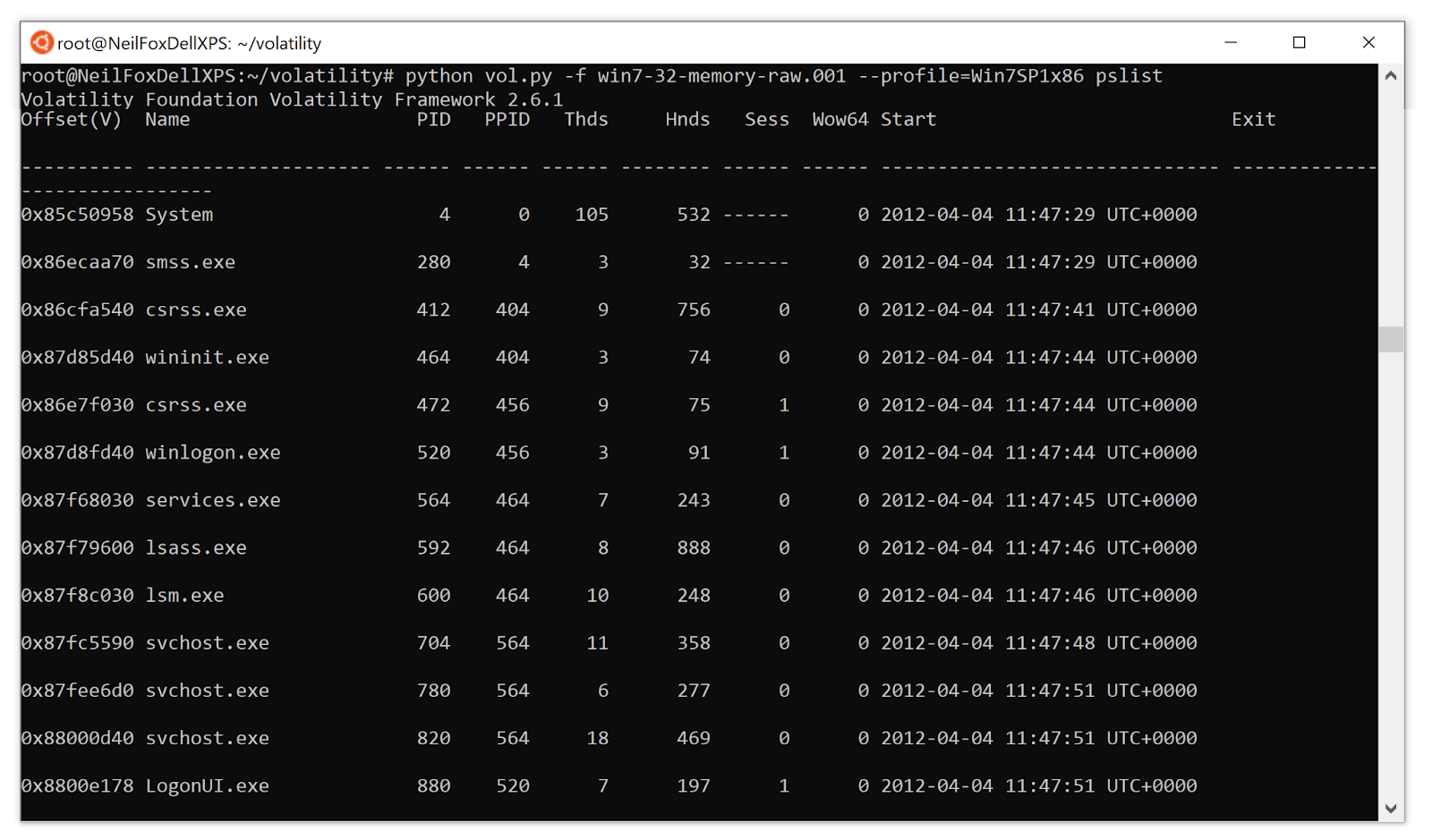
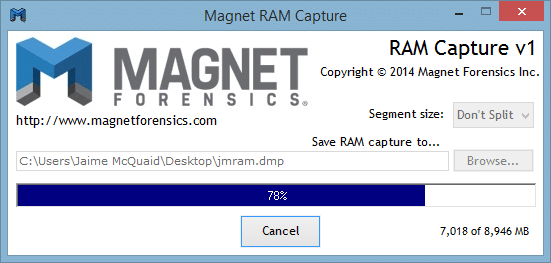
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 14 (Live Memory Forensics) « Null Byte :: WonderHowTo

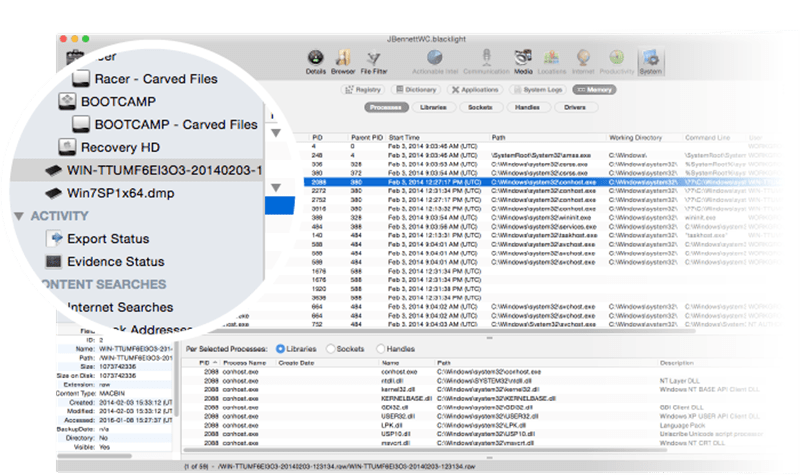
![PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5844da2c4456091748958bcc035ff8a52e6d8340/18-Figure1-1.png)